Catatan ini akan menjelaskan langkah-langkah untuk mengkonfigurasi koneksi SSL VPN Client Remote Access di Sophos XG Firewall, dimasa pandemi Covid-19 ini sangat dibutuhkan oleh perusahaan yang diharuskan karyawannya bekerja dari rumah (Work From Home) dengan tujuan mengakses server atau aplikasi yang berada di kantor dari jarak jauh.
Berikut Topologi & Skenarionya
| Location | JAKARTA | REMOTE USERS |
|---|---|---|
| Site | Head Office | Other Location |
| Device Name | Sophos XG 210 | Notebook/Handphone |
| Device Firmware | SFOS 18.5.4 MR4-Build418 | - |
| Device IP | 192.168.101.254 | - |
| LAN Subnet | 192.168.101.0/24 | 192.168.109.0/24 |
| LAN Port | Port6 | - |
| WAN Bandwidth | Dedicated 30 Mbps | - |
| WAN IP | 103.138.40.11 | - |
| WAN Port | Port1 | - |
| SSL VPN Protocol | TCP | - |
| SSL Server Certificate | CA_HLID | - |
| SSL VPN Port | 4443 | - |
| JKTFA01 IP | 192.168.101.231 | - |
| JKTFS01 IP | 192.168.101.241 | - |
Please note that for the first-time configuration of SSL VPN, it is required to edit the attributes of the default certificate of the Sophos Firewall to be able to make the SSL VPN configuration work. Follow the steps in Update Default CA to edit the default certificate.
1. Konfigurasi SSL VPN Client-to-Site Remote Access
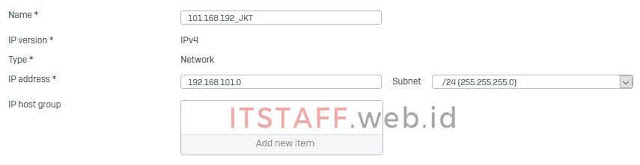
1.1. Login ke Sophos XG 210 Firewall, langkah pertama adalah menambahkan LAN Subnet Jakarta dan Remote User, klik SYSTEM Host and services ⇒ IP host ⇒ Add
- Local LAN (Jakarta Subnet)
- Remote User (SSL VPN Subnet)
- Save
1.2. Jika kalian sudah menghubungkan Sophos Firewall ke Active Directory server, kalian bisa SKIP 1.2 dan 1.2.1 atau ikuti panduan menambahkan Active Directory ke Sophos Firewall dan kalian bisa langsung login ke User Portal serta lanjut ke 1.3. SSL VPN Policy. Jika belum, kalian harus membuat Group SSL VPN, klik CONFIGURE Authentication ⇒ Groups ⇒ Add
- Group name* : VPN IT Group
- Group type* : Normal
- Surping quota* : Unlimited Internet Access
- Access time* : Allowed all the time
- Network traffic : None
- Traffic shaping : None
- Remote access* : No policy applied
- Clientless* : No policy applied
- Quarantine digest* : Enable
- MAC binding : Enable
- L2TP* : Disable
- PPTP* : Disable
Sophos Connect client* : Disable (default)- IPsec remote access* : Disable (default)
- Login restriction *: Any node
- Save
1.2.1. Selanjutnya adalah membuat User SSL VPN, klik CONFIGURE Authentication ⇒ Users ⇒ Add
- Username *: it.staff
- Name* : IT Staff
- Password* : Passwd it.staff
- User type* : Administrator
- Email* : it.staff@thehoneylady.co.id
- Group* : VPN IT Group
- Yang lain biarkan Default, nanti akan mengikuti pengaturan Group yang telah dibuat pada point 1.2.
- Save
1.3. Setelah itu, membuat SSL VPN Policy, klik CONFIGURE VPN ⇒ SSL VPN (remote access) ⇒ Add
- Name *: IT SSL VPN
- Policy members: VPN IT Group
- Use as default gateway: OFF
- Permitted network resource (IPv4): Local LAN
- Disconnect idle clients: OFF
- Save
1.4. Verifying the authentication services for Firewall and SSL VPN Authentication, click CONFIGURE Authentication ⇒ Services 'Firewall authentication methods' and 'SSL VPN authentication methods'
- Local: checked
- Apply
1.5. Verifying the allowed zones for SSL VPN, click SYSTEM Administration ⇒ Device access
- ZONE LAN (SSL VPN & User Portal): checked
- ZONE WAN (SSL VPN & User Portal): checked
- ZONE VPN (User Portal): checked
- Save
1.6. Configuring advanced SSL VPN settings, click CONFIGURE VPN ⇒ Show VPN settings
- Protocol *:
TCPUDP - SSL server certificate *: CA_HLID
- Override hostname :
- Port* : 4443
- IPv4 lease range* : 192.168.101.11 - 192.168.101.200
- Subnet mask* : /24 (255.255.255.0)
- IPv6 lease (IPv6/prefix)* : Default
- Lease mode* : IPv4 only
- IPv4 DNS : 192.168.101.251 - 192.168.101.252
- Domain name : thehoneylady
- Disconnect dead peer after* : 180 Seconds (default)
- Disconnect idle peer after* : 60 Minutes (default)
- Encryptografic algorithm : AES-256-CBC
- Authentication algorithm : SHA2 256
- Key size : 2048 bit
- Key lifetime : 28800 Seconds
- Compress SSL VPN traffic : checked
- Apply
1.7. Terakhir adalah membuat dua Firewall Rules SSL VPN Remote Access traffic, klik PROTECT Firewall (v17) / Rules and policies (v18) ⇒ + Add firewall rule ⇒ User/network rule
- 1.7.1. Group VPN to LAN
- Rule name *: VPN_LAN_REMOTE
- Action: Accept
- Log firewall traffic checked
- Rule position: Top
- Rule group: VPN to LAN
- Source
- Source zones * ⇒ Add new item: VPN
- Source networks and devices * ⇒ Add new item: 109.168.192_SSL_VPN_JKT
- During scheduled time: All the time
- Destination and services
- Destination zones * ⇒ Add new item: LAN
- Destination networks * ⇒ Add new item: 101.168.192_JKT
- Services *: Any
Identity (v17): Match known users: checkedShow captive portal to unknown users: unchecked- User or groups: VPN IT Group
Web malware and content scanning (v17)/ Security features (v18)- Web policy : None
- Scan FTP for malware checked
- Unchecked All
Advanced (v17)/ Other security features (v18)- App control : None
- IPS : None
- Shape traffic : None
- Scan email content : None
- Save
- 1.7.2. Group LAN to VPN
- Rule name *: LAN_VPN_REMOTE
- Action: Accept
- Log firewall traffic checked
- Rule position: Top
- Rule group: LAN to VPN
- Source
- Source zones * ⇒ Add new item: LAN
- Source networks and devices * ⇒ Add new item: 101.168.192_JKT
- During scheduled time: All the time
- Destination and services
- Destination zones * ⇒ Add new item: VPN
- Destination networks * ⇒ Add new item: 109.168.192_SSL_VPN_JKT
- Services *: Any
Identity (v17): Match known users uncheckedWeb malware and content scanning (v17)/ Security features (v18)- Web policy: None
- Scan FTP for malware checked
- Unchecked All
Advanced (v17)/ Other security features (v18)- App control: None
- IPS: None
- Shape traffic: None
- Scan email content: None
- Save
Berikut posisi atau penempatan Firewall Rules yang saya terapkan pada perangkat Sophos XG210 Firewall.
- LAN to VPN
- LAN_VPN_REMOTE (1.7.2)
- WAN to LAN
- LAN to WAN
- LAN to LAN
- VPN to LAN
- VPN_LAN_REMOTE (1.7.1)
Part #2. Install & Konfigurasi SSL VPN Client Windows
Part #2.1. Install & Konfigurasi SSL VPN Client Windows Sophos Connect
Part #3. Install & Konfigurasi SSL VPN Client Mac OS X
Part #4. Install & Konfigurasi SSL VPN Client Android
Part #5. Install & Konfigurasi SSL VPN Client iPhone/iPad
Selesai, itu saja yang saya lakukan untuk membuat koneksi SSL VPN Remote Access di Sophos XG210 Firewall, konfigurasi di atas bisa juga diterapkan pada Sophos XG Firewall Series dengan firmware v17, v18. Semoga catatan ini bisa berguna untuk saya dan kalian yang membacanya.