Catatan ini akan menjelaskan langkah-langkah untuk membuat koneksi IPsec VPN Site-to-Site Preshared Key antara Sophos XG Firewall dan Cyberoam Firewall. Dimana salah satu group kami di Batam sudah menggunakan perangkat Cyberoam CR50ia Firewall.
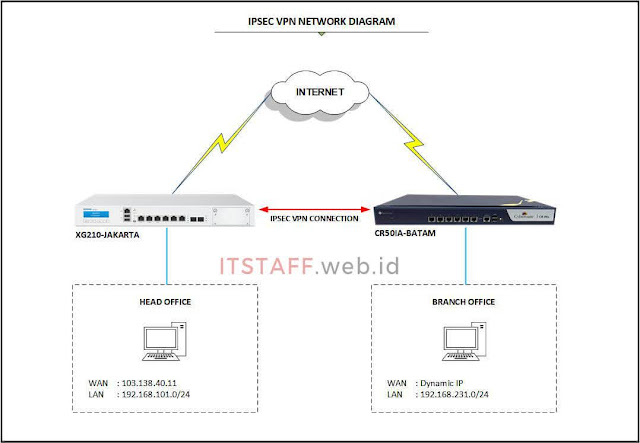
Berikut Topologi & Skenarionya
| Location | JAKARTA | BATAM |
|---|---|---|
| Site | Head Office | Branch Office |
| Device Name | Sophos XG 210 | Cyberoam CR50ia |
| Device Firmware | SFOS 18.5.4 MR4-Build418 | 10.6.6 MR-3-Build305 |
| Device IP | 192.168.101.254 | 192.168.231.254 |
| LAN Subnet | 192.168.101.0/24 | 192.168.231.0/24 |
| LAN Port | Port6 | PortF |
| WAN Bandwidth | Dedicated 30 Mbps | Shared 100 Mbps |
| WAN IP | 103.138.40.11 | Dymanic IP Public |
| WAN Port | Port1 | PortA |
| IPsec Connection Type | Site-to-Site | Site-to-Site |
| IPsec Gateway Type | Respond only | Initiate the connection |
| IPsec Policy | DefaultHeadOffice | DefaultBranchOfficeXG |
| IPsec Authentication Type | Preshared key | Preshared key |
Oke lah kalau begitu, tanpa basa-basi lagi, langsung saja mari kita mulai konfigurasi...
1. Konfigurasi XG210-JAKARTA - Head Office
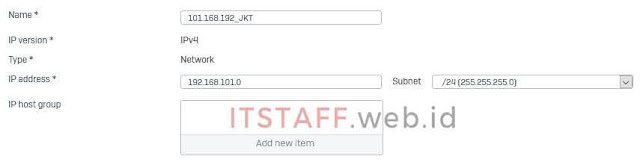
1.1. Login ke Sophos XG210 Firewall, langkah pertama adalah menambahkan LAN Subnet (Jakarta dan Batam), klik SYSTEM Host and services ⇒ IP host ⇒ Add
- Local LAN (Jakarta Subnet)
- Remote LAN (Batam Subnet)
- Save
1.2. Sekarang membuat IPsec VPN connection, klik CONFIGURE VPN ⇒ IPsec connections ⇒ Add
- General settings
- Name: VPN_BATAM
- IP version: IPv4
- Connection type: Site-to-Site
- Gateway type: Respond only
- Active on save checked
- Create firewall rule unchecked
- Encryption
- Policy: DefaultHeadOffice
- Authentication type: Preshared key
- Preshared key: <Password IPsec>
- Repeat preshared key: <Password IPsec>
- Gateway settings
- Listening interface: Port1 (WAN1)
- Local ID type: Select local ID (default)
- Local subnet: Add new item ⇒ 101.168.192_JKT Remote gateway
- Gateway address: *
- Remote ID type: Select remote ID (default)
- Remote subnet: Add new item ⇒ 231.168.192_BTM
- Network Address Translation (NAT) unchecked
- Advanced: User authentication mode: None
- Save
-
Local gateway
1.3. Setelah itu, membuat dua Firewall Rules untuk IPsec VPN traffic, klik PROTECT Firewall (v17) / Rules and policies (v18) ⇒ + Add firewall rule ⇒ User/network rule
- 1.3.1. Group LAN to VPN
- Rule name *: LAN_VPN_BATAM
- Action: Accept
- Log firewall traffic checked
- Rule position: Top
- Rule group: LAN to VPN
- Source
- Source zones *: Add new item ⇒ LAN
- Source networks and devices *: Add new item ⇒ 101.168.192_JKT
- During scheduled time: All the time
- Destination and services
- Destination zones *: Add new item ⇒ VPN
- Destination networks *: Add new item ⇒ 231.168.192_BTM
- Services *: Any
Identity (v17): Match known users uncheckedWeb malware and content scanning (v17)/ Security features (v18)- Web policy: None
- Scan FTP for malware checked
- Unchecked All
Advanced (v17)/ Other security features (v18)- App control: None
- IPS: None
- Shape traffic: None
- Scan email content: None
- Save
- 1.3.2. Group VPN to LAN
- Rule name *: VPN_LAN_BATAM
- Action: Accept
- Log firewall traffic checked
- Rule position: Top
- Rule group: VPN to LAN
- Source
- Source zones *: Add new item ⇒ VPN
- Source networks and devices *: Add new item ⇒ 231.168.192_BTM
- During scheduled time: All the time
- Destination and services
- Destination zones *: Add new item ⇒ LAN
- Destination networks *: Add new item ⇒ 101.168.192_JKT
- Services *: Any
Identity (v17): Match known users uncheckedWeb malware and content scanning (v17)/ Security features (v18)- Web policy: None
- Scan FTP for malware checked
- Unchecked All
Advanced (v17)/ Other security features (v18)- App control: None
- IPS: None
- Shape traffic: None
- Scan email content: None
- Save
Berikut posisi atau penempatan Firewall Rules yang saya terapkan pada perangkat Sophos XG210 Firewall.
- LAN to VPN
- LAN_VPN_BATAM (1.3.1)
- WAN to LAN
- LAN to WAN
- LAN to LAN
- VPN to LAN
- VPN_LAN_BATAM (1.3.2)
2. Konfigurasi CR50IA-BATAM - Branch Office
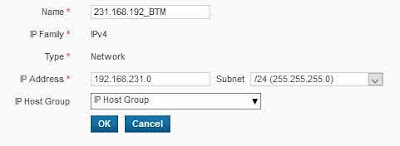
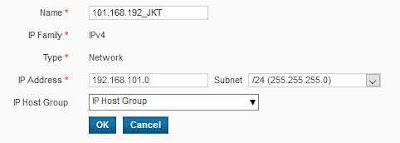
2.1. Login ke Cyberoam CR50ia Firewall, langkah pertama adalah menambahkan LAN Subnet (Batam dan Jakarta), klik OBJECTS Hosts ⇒ IP Host ⇒ Add
- Local LAN (Batam Subnet)
- Remote LAN (Jakarta Subnet)
- OK
2.2. Selanjutnya adalah membuat IPsec Profile, disini saya mengikuti parameter IPsec Profile DefaultBranchOffice dari Sophos XG210, klik VPN Policy ⇒ Add
- General Settings
- Name*: DefaultBrachOfficeXG
- Allow Re-keying: Enable checked
- Key Negotiation Tries*: 0
- Authentication Mode*: Main Mode
- Pass Data In Compressed Format: uchecked
- Phase 1
- Encryption Algorithm*: AES256
- Encryption Algorithm*: SHA2 256
- DH Group (Key Group)*: 14(DH2048) 15(DH3072) 16(DH4096) checked
- Key Life*: 10800
- Rekey Margin*: 540
- Randomize Re-Keying Margin By*: 100 %
- Dead Peer After Detection: Enable checked
- Check Peer After Every: 30 Seconds
- Wait For Response Upto: 120 Seconds
- Action When Peer Unreachable: Re-initiate
- Phase 2
- Encryption Algorithm*: AES256
- Encryption Algorithm*: SHA2 256
- PFS Group (DH Group)*: Same as Phase-I
- Key Life* : 3600
- OK
2.3. Setelah membuat IPsec Policy, selanjutnya adalah membuat IPsec VPN Connection, masih di VPN IPSec ⇒ Connection ⇒ Add
- General settings
- Name*: VPN_JAKARTA
- Connection Type*: Site-to-Site
- Policy*: DefaultBranchOfficeXG
- Action on VPN Restart*: Initiate
- Route Based Connection
- Bind With An Interface: Enable unchecked
- Authentication Details
- Authentication Type*: Preshared Key
- Preshared Key*: <Password IPsec>
- Enpoints Details
- Local*: PortA
- Remote*: 103.138.40.11
- Network Detail
- IP Family*: IPv4
- Local
- Local Subnet*: Add ⇒ 231.168.192_BTM
- NATed LAN: Same as Local LAN address
- Local ID: Select Local ID (default)
- Remote
- Allow NAT Traversal: unchecked Enable
- Remote LAN Network*: 101.168.192_JKT
- Remote ID: Select Remote ID (default)
- User Authentication
- User Authentication Mode*: Disable
- Quick Mode Selectors
- Protocol*: All
- OK
2.4. Setelah itu, membuat dua Firewall Rules untuk IPsec VPN traffic, klik FIREWALL Rule ⇒ Add
- 2.4.1. Group LAN - VPN
- Rule Name*: LAN to VPN
- Basic Settings
- Source
- Zone*: LAN
- Attach Identity: unchecked
- Network/Host*: Add ⇒ 231.168.192_BTM
- Services*: Any Services
- Schedule: All The Time
- Action*: Accept
- Destination
- Zone*: VPN
- Network/Host*: Add ⇒ 101.168.192_JKT
- Security Policies: None & Unchecked All
- QoS & Routing Policy: None
- Log Traffic: Enable checked
- OK
- 2.4.2. Group VPN - LAN
- Rule Name*: VPN to LAN
- Basic Settings
- Source
- Zone*: VPN
- Attach Identity: unchecked
- Network/Host*: Add ⇒ 101.168.192_JKT
- Services*: Any Services
- Schedule: All The Time
- Action*: Accept
- Destination
- Zone*: LAN
- Network/Host*: Add ⇒ 231.168.192_BTM
- Security Policies: None & Unchecked All
- QoS & Routing Policy: None
- Log Traffic: Enable checked
- OK
Berikut posisi atau penempatan Firewall Rules yang saya terapkan pada perangkat Cyberoam CR50ia Firewall.
- LAN - VPN
- LAN to VPN (2.4.1)
- WAN - LAN
- LAN - WAN
- LAN - LAN
- VPN - LAN
- VPN to LAN (2.4.2)
3. Pengujian Tunnel IPsec VPN Site-to-Site Connections
Dengan konfigurasi diatas, harusnya tunnel IPsec VPN Site-to-Site sudah terbentuk. Kalian bisa cek statusnya di Sophos XG210 Jakarta & Cyberoam CR50ia Batam.
- Status di XG210-JAKARTA, klik CONFIGURE VPN ⇒ IPsec connections
- Status di CR50IA-BATAM, klik VPN IPSec ⇒ Connection
Jika Status Active dan Connection sudah berwarna hijau, sekarang coba test ping dari perangkat di bawah Firewall, misal dari komputer desktop lokal di masing-masing site Jakarta maupun Batam untuk memastikan koneksi IPsec VPN Site-to-Site ini berjalan dan bekerja. Jika masih Request time out, silahkan cek Rules and Policies Firewall (LAN to VPN & VPN to LAN).
Selesai, itu saja yang saya lakukan dalam membuat koneksi IPsec VPN Site-to-Site Preshared Key di Sophos XG210 dan Cyberoam CR50ia, konfigurasi di atas bisa juga diterapkan pada Sophos XG Firewall Series maupun Cyberoam Firewall Series. Semoga catatan ini bisa berguna untuk saya dan kalian yang membacanya.
1. Make sure that VPN Firewall Rules are on the top of the Firewall Rule list.
2. In a Head and Branch Office configuration, the Cyberoam Firewall on the Branch office usually acts as the tunnel initiator and the Sophos Firewall on the Head Office as a responder due to the following reasons:
- When the Branch Office device is configured with a Dynamic IP address, the Head Office device cannot initiate the connection.
- As the Branch Offices number vary, it is recommended that each Branch Office retry the connection instead of the Head Office retrying all connections to Branch Offices.